Harnessing the Power of Ethical Hacking: Unveiling Digital Vulnerabilities Safely
In today's era of rapid technological advancements, the ever-present threat of cyber attacks looms over individuals and organizations alike. To combat this ongoing battle, the practice of ethical hacking has emerged as a powerful tool in safeguarding our digital landscape. Ethical hacking, also known as white hat hacking, involves the use of highly skilled professionals to identify and expose vulnerabilities in computer systems, networks, and applications. By simulating real-world cyber attacks, these experts help organizations strengthen their security measures and fortify their defenses against malicious hackers.
Unlike their nefarious counterparts, ethical hackers operate with the noble intention of enhancing overall system security rather than causing harm. These individuals possess a unique combination of technical expertise, analytical thinking, and ethical responsibility. Serving as a vital bridge between the realms of cybersecurity and hacking, they employ a wide range of techniques and methodologies to stress-test systems and probe for potential weaknesses. Their ultimate goal is not to exploit vulnerabilities but to uncover them and help organizations reinforce their digital fortresses.
The utilization of ethical hacking has gained significant recognition and acceptance in recent years, with numerous companies and institutions recognizing its value in proactively addressing security concerns. By engaging the services of ethical hackers, enterprises can proactively identify vulnerabilities, close security gaps, and prevent unauthorized access to their systems. This proactive approach not only helps prevent cyber attacks but also instills trust and confidence among customers, partners, and stakeholders. In a time where data breaches and cybercrimes continually make headlines, investing in ethical hacking has become an essential strategic move for organizations across industries.
Benefits of Ethical Hacking
Ethical hacking, also known as "white hat" hacking, involves authorized individuals using their skills to identify and uncover vulnerabilities in computer systems. This approach offers several benefits that can significantly enhance the security and resilience of digital infrastructure.
-
Improved Security Measures: By employing ethical hackers, organizations can proactively identify weaknesses in their systems before malicious actors exploit them. These professionals simulate real-world attack scenarios, providing valuable insights into potential vulnerabilities. With this information, organizations can take proactive steps to strengthen their defenses, reducing the risk of unauthorized access or data breaches.
-
Enhanced Risk Assessment: Ethical hacking helps organizations gain a comprehensive understanding of their risk landscape. By identifying and assessing potential vulnerabilities, they can prioritize their security efforts and allocate resources effectively. This proactive approach allows organizations to focus on addressing critical vulnerabilities and reducing the overall risk to their digital assets.
-
Compliance and Audit Support: Ethical hacking is instrumental in meeting regulatory requirements and industry standards. Many sectors, such as finance and healthcare, have specific security regulations that organizations must adhere to. Conducting regular ethical hacking assessments helps ensure compliance and provides evidence of due diligence during audits.
-
Enhanced Incident Response: By regularly testing their systems through ethical hacking, organizations can improve their incident response capabilities. By identifying and resolving vulnerabilities, they can better prepare for potential cyberattacks. This proactive approach strengthens an organization's ability to detect, contain, and mitigate the impact of security incidents, minimizing potential disruptions to their operations.
-
Trust and Reputation: Employing ethical hackers demonstrates a commitment to protecting sensitive data and customer information. By investing in robust security measures, organizations can foster trust among their stakeholders. This commitment to security can enhance their reputation and ultimately attract more customers who value data protection.
In conclusion, ethical hacking provides numerous benefits to organizations, including improved security measures, enhanced risk assessment capabilities, compliance support, enhanced incident response preparation, and bolstered trust and reputation. By embracing this approach, organizations can stay one step ahead in the ever-evolving landscape of cybersecurity threats.
Choosing the Right Ethical Hacker
When it comes to harnessing the power of ethical hacking, finding the right professional is crucial. With the prevalence of digital vulnerabilities, organizations must be diligent in selecting an ethical hacker who possesses the necessary skills and expertise.
First and foremost, consider the hacker's qualifications. Look for individuals who have a strong background in computer science, information technology, or related fields. A solid educational foundation combined with relevant certifications, such as Certified Ethical Hacker (CEH), can indicate the hacker's commitment to their craft.
Additionally, experience plays a vital role in determining the right ethical hacker for your needs. Look for hire a hacker who have a proven track record in identifying and addressing vulnerabilities. An experienced ethical hacker should be well-versed in different hacking techniques and possess a deep understanding of complex systems.
Moreover, consider the hacker's reputation and ethics. Ethical hacking requires a high level of integrity and professionalism. Seek out individuals who adhere to ethical guidelines and prioritize the security and privacy of your organization. Research their previous engagements and verify their reputation within the cybersecurity community.
In conclusion, choosing the right ethical hacker is essential for organizations aiming to unveil digital vulnerabilities safely. By considering qualifications, experience, and reputation, you can find a professional who possesses the necessary expertise and upholds ethical principles in their work.
Implementing Ethical Hacking Safely
When it comes to harnessing the power of ethical hacking, it is essential to prioritize safety and security. By taking appropriate measures, organizations can effectively uncover digital vulnerabilities without compromising their systems. Here are some key considerations for implementing ethical hacking in a safe manner.
-
Planning and Consent:
Before commencing any ethical hacking activities, it is crucial to have a well-defined plan in place. This plan should outline the scope, objectives, and limitations of the hacking engagement. Additionally, obtaining informed consent from all relevant stakeholders is paramount. Clear communication and documentation ensure that everyone involved understands the purpose and potential risks of the hacking process. -
Engaging Skilled Professionals:
To safely execute ethical hacking, organizations should hire experienced professionals who possess the necessary skills and expertise. These individuals understand the legal and ethical boundaries of hacking and can navigate complex systems without causing harm. Opting for certified ethical hackers or reputable security firms can provide an added layer of assurance.
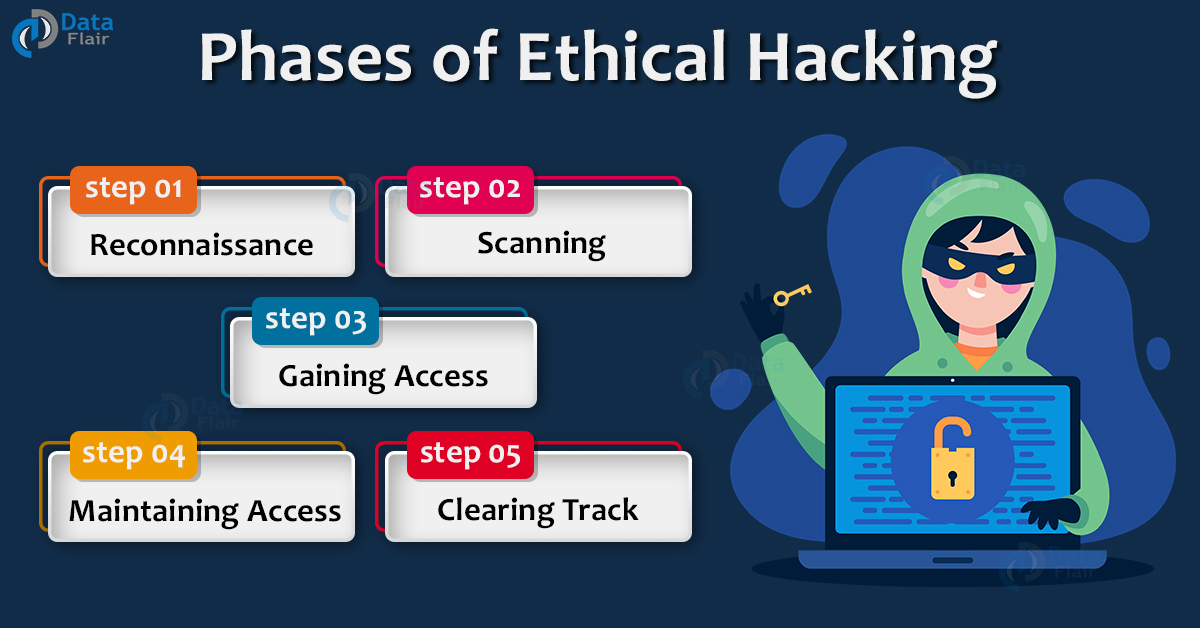
-
Establishing a Controlled Environment:
Creating a controlled testing environment is crucial to avoid unintended consequences. Setting up a separate network or working with virtual machines can help isolate the testing process from the main infrastructure. This containment minimizes the likelihood of accidental damage and facilitates easier monitoring and management of the hacking activities.
By implementing ethical hacking safely, organizations can proactively identify and address vulnerabilities before malicious actors exploit them. The safeguards put in place ensure a responsible and secure approach to protecting sensitive digital assets.