Analyzing Different Proxy Types: An Explanation of the Differences
In the current digital landscape, utilizing proxies has become vital for a multitude of online activities, from web scraping to maintaining privacy and anonymity. As businesses and individuals navigate through the complexities of the internet, understanding the various types of proxies and each one's functionalities is important. This article seeks to break down the various proxy types, exploring the differences and how they can be efficiently utilized for optimal results.
Whether you are looking to scrape data from online platforms, verify proxy servers, or guarantee secure browsing, the appropriate tools can make all the impact. We will delve into key concepts such as proxy scrapers, proxy checkers, and the distinction between HTTP and SOCKS proxies, while also offering insights into the best sources for high-quality proxies. As the rise of free and paid options, knowing how to select the most suitable proxy for your needs will empower you to navigate the internet more efficiently and securely.
Understanding Types of Proxies
Proxy servers serve as intermediaries between a client and the internet, facilitating multiple types of links. These include HTTP, SOCKS4, and SOCKS5 proxies, each designed for particular applications. HTTP proxies are commonly employed for browsing the web and scraping data, focusing primarily on HTTP or HTTPS data. SOCKS proxies, on the other hand, can support all kinds of traffic, allowing them to transmit data for various Protocols beyond just internet traffic, thus making them flexible for different uses.
As considering proxies for web scraping, knowing the distinction between public and private proxies is essential. Open proxies, which are often free, are shared among numerous users and can be slow and inconsistent. In comparison, dedicated proxies are used exclusively by a single user, providing improved speed and dependability, making them ideal for tasks that require steady performance. This distinction is critical, especially when speed and privacy are key factors in extracting data tasks.
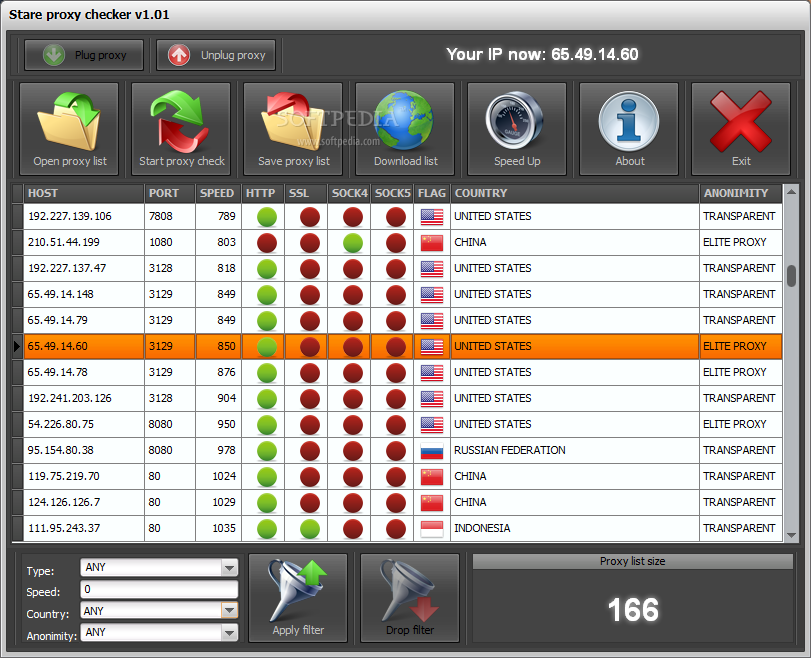
Additionally, the efficiency of a proxy server depends on its quality. High-quality proxies can significantly impact scraping success, helping users avoid IP bans and slowdowns. Applications to check the speed of a proxy and anonymity, such as proxy checkers and verification tools, play a critical role in making sure that only the most dependable proxies are employed. Learning how to locate and test proxies efficiently is essential for achieving desirable outcomes in data scraping and other automated processes.
Proxy Scraper Utilities
Proxy scraping tools are essential instruments for anyone seeking to collect proxies from multiple sources online. These tools streamline the process of searching for and collecting proxy servers, enabling individuals to develop their personal proxy lists rapidly and effectively. With a variety of options available, including free proxy scrapers and paid editions, users can select a tool that matches their individual requirements and budget.
One of the main attributes of a high-quality proxy scraper is its capacity to sort proxies based on certain criteria, including latency, level of anonymity, and protocol type. Tools like the speedy proxy scraper and HTTP proxy scraper are well-liked among individuals who require targeted functionalities. Additionally, proxy scraping with Python excel in gathering proxies for data scraping tasks, providing users with a robust list of proxy servers that can be used for data extraction without getting blocked.
For those who need trustworthy and verified proxies, a proxy testing tool is known to be important. This tool verifies the effectiveness and discretion of collected proxies, making sure that users are working with top-notch sources. By merging a proxy scraper with a proxy verifier, users can streamline their workflow and enhance their web scraping efforts, resulting in the task of finding and using proxies much more feasible.
Proxy Checking Methods
When it comes to verifying the efficacy of proxies, there are multiple methods to confirm that they fulfill the required specifications. One of the most common approaches is to use a proxy checker, which tests the proxy servers for availability, speed, and privacy protection. This utility systematically sends queries through the proxies to assess whether they are operational and if they can support the desired amount of load. Knowing the performance statistics is crucial for clients who need dependable proxy servers for activities such as web scraping or automation.
A further valid approach is hands-on evaluation, where users connect to their desired software or websites via the proxy server and evaluate the availability and speed directly. This approach can help identify problems like latency or blacklisted IP addresses that software solutions might miss. Additionally, clients can review header information to understand the type of proxy server they are working with, determining whether they are utilizing Hypertext Transfer Protocol, SOCKS4, or SOCKS5 proxy servers.
Lastly, verifying proxy server anonymity is vital for clients worried about privacy and security. Various online tools can evaluate how transparent a proxy is, allowing clients determine whether their real IP address is being exposed. Best recommendations suggest that clients regularly test their proxy servers as part of maintenance, especially if relying on them for confidential operations or large-scale web scraping initiatives. By implementing these proxy verification techniques, clients can ensure reliable, top-notch functionality.
Differences Between Hypertext Transfer Protocol and Socket Secure Proxies
HTTP proxies are specially designed to handle data flow from browser applications while are optimized towards web-based applications. They operate at the app layer of the Open Systems Interconnection model while tend to be commonly used for obtaining website content. This type of server can store content, filter traffic, as well as execute multiple tasks that enhance the browsing experience. However, HTTP proxies tend to be not typically appropriate with non-HTTP traffic, indicating all requests that may not relate to web browsing may encounter issues when sent via an HTTP proxy.
On the other hand, Socket Secure proxies offer a greater versatile solution as they functioning at the transportation layer. They can be capable to managing different types of internet data flow, including Hypertext Transfer Protocol, File Transfer Protocol, and others, which makes them appropriate for applications beyond simple internet navigation. SOCKS proxies tend to be especially beneficial for tasks like file sharing and any interactions which necessitate a more strong protocol capabilities. SOCKS version 5, the most recent version, features extra features like authentication and compatibility for both IPv4 and IPv6, making them perfect for individuals looking for high privacy and versatility.
As you are selecting among HTTP and Socket Secure proxy servers, one should crucial that you think about the particular application scenario. In the case of typical data extraction or internet navigation tasks, an HTTP proxy may be sufficient, especially when caching and content filtering prove to be helpful. Conversely, if an app needs the capability to support various protocols and demands privacy, a SOCKS server is likely to be a better fit. Grasping these differences can help in choosing the right proxy type for effective and safe online activities.
Employing Proxy Servers for Data Extraction
Proxy Servers are vital assets for data extraction, enabling users to acquire content from websites without the danger of being restricted. When extracting data, it's common for servers to detect and limit repeated requests from the identical IP address. By using a proxy scraper, individuals can get a variety of IP addresses, allowing them to spread their requests across various sources. This not only helps maintain access to the target site but also lowers the likelihood of initiating security protocols that could hinder the scraping efforts.
When it comes to picking proxy servers for web scraping, grasping the distinctions between categories such as Hypertext Transfer Protocol, SOCKS version 4, and SOCKS5 is important. HTTP proxy servers are primarily created for web traffic, while SOCKS proxies can handle any form of traffic and are often more versatile. This flexibility is particularly advantageous for scraping tasks that require various protocols. Additionally, using tools like a proxy checker or verification tool can assist ensure that the chosen proxies are working and meet speed and concealment requirements.
In the future, the landscape of costless proxies keeps to evolve, making it crucial to use the best no-cost proxy testing tools and scrapers. These resources facilitate effective data extraction and can help in identifying high-quality proxy servers. Many web scraping projects leverage automation with proxies, using strategies that balance the use of exclusive and public proxies to enhance information gathering rates while reducing the likelihood of being discovered. Comprehending how to efficiently find and use proxy servers will improve your capability to collect data swiftly and reliably across multiple platforms.
Analyzing Proxy Server Performance and Anonymity
As assessing proxy servers for tasks such as web scraping or automation, speed is a crucial factor. A quick proxy connection minimizes latency and improves overall performance, allowing for more rapid data retrieval. To evaluate proxy speed, one can employ dedicated testing applications, often referred to as proxy checkers. These tools not only check the connection speed but can also ping the proxy to find out response times across multiple regions, ensuring users can opt for the most efficient options for their unique needs.
Anonymity is another crucial aspect when evaluating proxies. Various kinds of proxies provide different levels of privacy, from open to elite. Evaluating a proxy's level of anonymity involves checking whether it shows the user's original IP address or any personal information. Tools designed for proxy verification can help users assess if a proxy is anonymous, high-anonymity, or transparent, guaranteeing that the opted proxies align with the necessary security standards for web scraping or other tasks.
Overall, understanding the balance between speed and privacy is essential for effective proxy utilization. High-speed proxies are ideal for rapid data collection, but if they undermine user anonymity, the trade-off might not be worth it. Evaluating proxies based on both parameters enables users to reach informed decisions, ensuring that they use proxies that both perform well but also safeguard their digital identity while engaging in activities such as web scraping or automation.
Choosing the Most Effective Proxies for Automating Tasks
While performing tasks over the internet, selecting the right proxies is vital for attaining effectiveness. First, evaluate the type of proxies that will most fit your purposes. Dedicated proxies offer greater anonymity and stability, which makes them appropriate for tasks that require elevated reliability. Alternatively, public proxies can be a no-cost option but may cause slow speeds and lower security. Understanding the differences between these categories will help simplify your automation processes.
Subsequently, assess the speed and uptime of the proxies you are looking at. Fast proxy tools are crucial for tasks that require large-scale data scraping or live interactions. Tools such as proxy testers are valuable for checking the reactivity and availability of proxies before utilization. Ensuring you have a fast and dependable proxy list can boost your automation's efficiency significantly, enabling you to perform tasks effectively.
In conclusion, checking proxy anonymity is essential to protect your operations. Use a proxy verification tool to find out how well your proxies hide your original IP address. This will not only protect your identity but also lessen the risk of being banned by websites. By focusing on quality sources and employing best practices for locating high-quality proxies, you can effectively boost your automation tasks and overall data extraction efforts.