pcTattletale Writeup
UPDATE: pcTattletale has permanently shutdown, source
NOTICE: Due to pcTattletale going offline, we have limited screenshots from the application
pcTattletale is a simple piece of spyware designed to be silently planted on someone’s computer by someone who has access to it, such as a spouse, or parent. However, pcTattletale has many security and privacy issues beyond just being spyware.
Member IDs and Device IDs are sequential
Lets start off with a relatively mundane vulnerability, pcTattletale (from here on referred to as PCTT) stores its Member IDs and Device IDs in sequential order. This makes it easy to enumerate accounts (will be important later) and can be used to expose how many users and devices are on the PCTT service.
Name your price billing, on accident
What if I told you, you could have the pcTattletale software with 365 days of data retention, and 2147483647 devices for the low, low price of 1 American Cent per year? You’d probably still say that’s too much to pay for this software, and I’d agree. On the checkout page to upgrade your PCTT account from a free trial to a paid account, the payment flow is entirely managed by query strings in the URL bar. Now this can be done properly, notice keyword can. Let’s look at how PCTT does it:
There are three query parameters:
- plan, which controls what tier of data retention and how long the plan lasts for
- qty, which specifies the quantity of devices on the account allowed
- id, which controls the PRICE of your purchase
Now PayPal, PCTT’s chosen payment gateway, will not let you purchase an item that costs zero dollars. However, they will let you purchase an item that costs one American Cent. So how do I go about getting this steal of a deal? It’s simple:
If you are logged into a PCTT account, and go to that link, you can make the purchase I talked about in the beginning of the section, with zero issue.
Honestly I'm really not sure why PCTT has this flaw, it’s an extremely simple thing not to do, or at least make slightly more difficult by not putting the price in the URL bar, and instead putting it in the client side website code. Now that’s still bad, your entire payment flow should be handled server side, especially when defining product prices, but that would at least make this attack slightly less trivial.
Because why follow one law when your already breaking the rest?
You might try out pcTattletale, install it on your [wife, husband, child]’s computer, and realize that it’s not cool to spy on other people without them knowing. So now with this new change of heart, what are you going to do with your PCTT account? Well of course your going to delete it. So you delete your account. You think to yourself “I’m glad all of my personal information has been deleted from their servers.” I have news for you my friend, PCTT does NOT delete user data when you delete your account, or delete a device from your account. If we look at our network logs while we still have our PCTT account, and the device is still on the account, we can see requests to PCTT’s S3 bucket. This bucket is where all the data collected by the PCTT spyware is stored. Let’s go ahead and save one of these URLs for later.
Now let’s delete the device from our PCTT account, and see if we can still access this image:
The image is still accessible
Hm, the image is still accessible. Even though I’ve deleted this device from my account. That’s odd, let’s try deleting my entire PCTT account and see if it’s still there:

The image is still accessible, even after deleting the PCTT account and device
Well, I think that tells you everything you need to know about this app. Even after deleting the device from my account, and then my ENTIRE account, my data is still being held onto by PCTT. It gets worse, if you try to sign up for another account using the same email address, you’ll get the following message:
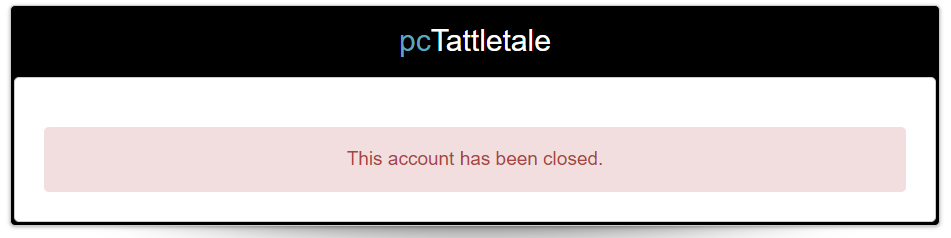
I smell GDPR violations
This means that PCTT is not only retaining your data, but retaining it in such a manner that it can still be used to identify you. If the data was stored in a manner that made it unidentifiable, you could create a new account with the same email address, as there would be no record of that email in their systems.
This is a major privacy, and legal issue with this software. Be warned that ANYTHING sent to this service will be stored indefinitely, even if you delete your account. If it’s keyloggers ever sniff a password, or it’s screen monitoring ever watches you view your bank details, it will be logged to their S3 bucket, permanently. There is no user facing, self service process to remove your data.
When it rains, it pours
So your data is stored indefinitely by PCTT, that’s bad. You might think, can it get any worse? Yes it can. Not only are your screenshots stored indefinitely, they are stored on a PUBLIC S3 BUCKET accessible to ANYONE who can get access to the URL (this is one place where the sequential IDs cause a problem). PcTattletale’s method for securing your most sensitive data is effectively the Powerball lottery, guess the numbers, win someone's data. Also, the icing on the cake, this flaw has been public and known for about 3 years. Source
All it takes is a Peek
PCTT uses Microsoft dotNet framework for it’s windows spyware. Now there’s something important to understand about dotNet executables, and that’s that they can be decompiled to their fully readable C# source code using a tool called dotPeek by JetBrains. By decompiling the PCTT executables you can find many endpoints and routes on both their dashboard, and AWS Lambda functions. It also completely spills all the secrets about this software and what it’s doing. This will be important later.
All roads lead home
PCTT likes to sell their spyware as “untraceable” and that your victim wont know they’ve had this software installed on their computer or phone. As is common with this program, things aren’t as they seem. PCTT leaves many, many traces on Windows including in the Task Manager startup programs and in the the Program Files directory. Also, in order to install the program, often times the person installing it has to setup whitelists in the victim’s antivirus programs, leaving yet another trace. On Android it’s even worse, requiring your victim’s launcher to support hiding apps, and having a casting icon in the menu bar constantly reminding your victim they are being watched.
Hunted becomes Hunter
You might think, well at least the person I’m spying on can’t access my account. Right? Wrong. So whenever you install PCTT on a computer, it has to register with the PCTT service to get a DeviceID, so here’s what that process looks like:
- Make a POST request to an AWS Lambda with JSON encoded in the body:
- The MemberID
- The computer’s name as DeviceName
- An empty DeviceDescription
- And the SoftwareVersion of the PCTT client
- This will return a JSON body with a few things but the important one’s are:
- The DeviceID
- And the AuthKey
- PCTT will save the AuthKey to:
- C:\Program Files (x86)\Common Files\Microsoft Shared\scheduler\authkey.dat
- Future requests to the PCTT service to upload screenshots and keylogs will use that authkey
Now we already know that we can look inside the PCTT application from what we learned in “All it takes is a Peek” so let’s use that to our advantage. When we look inside the application we find a very peculiar route:
So I opened an incognito window that wasn’t logged into the PCTT account, and I went to the above URL, appending the authkey from the authkey.dat file. You’ll never guess what happens next, you are logged into the PCTT account that installed spyware on your device, no password, no email needed.
To say this is an enormous flaw would be a gross understatement, considering the fact that this exposes:
- The email address of the person spying on you
- Everything they have collected on you
- When they started spying on you
- And allows the user to remove their device from your account
Really makes one cent per year sound like a hefty price for this doesn’t it? When your one job is to spy on people undetected, and somehow not only do you manage to get detected, you also manage to COMPROMISE the anonymity of the person using and paying for your software, what is your software really good for in the first place? Stay tuned, it gets worse.
Destination: Compromise
So far, everything we’ve seen is bad, terrible, even catastrophic, but it only gets worse. So all of my account data is public, if I delete my account or devices from my account, all my data is still saved, I can get this software for practically free, my victim can easily see that I am stalking them, and even get MY email address and see how long I’ve been stalking them. Now lets think back to the last section, and the very first section. Member IDs are sequential, and you need a MemberID to create a device, which in turn gives you an AuthKey, which can be used to get access to the MemberIDs account, including their PII and the collected PII of anyone they installed this software on. This means with a pretty short script, you could scrape the ENTIRE database of this website. All users emails, victims, screenshots, keylogs, everything can be scraped, even after someone deletes their account. You don’t even need to know the person using this software, you can just iterate, adding a device to every PCTT member’s account and using the generated key to scrape their data. Now this is great for a mass data leak attack, but what if you feel like doing something more targeted?
When attacks become personal
So lets say I knew a specific owner’s email address of a specific franchise of hotels who use PCTT on their computers. Normally, this wouldn’t be any kind of an issue. Password resets require you to have access to the inbox to get the password reset code for the account your resetting. PCTT however, is special. See, there is one very critical thing you CANNOT under any circumstances mess up on a self service, email based, password reset page. That is leaking the password reset token to the client. Well, PCTT doesn’t use code based password reset, they just change your password. The issue is that, they print the password TO THE CLIENT SIDE CONSOLE. If you go on the password reset page at PCTT, and request a password reset for an email while your console is open, there will be a UUID logged to the console prefixed by “Succes - “ typo included. The first 6 characters of that UUID are now the password of the account you just tried to password reset.
There are no words to describe how simply atrocious this is. This makes hacking someone who uses PCTT as simple as knowing their email address.
When images error
In the section where I talk about how you can create a device on PCTT without needing to install the agent on the device, I mention that you have to have a device name. As is common for this software that would make any security engineer or privacy advocate perish upon witnessing the utter terror known as this applications “security”, there’s yet another vulnerability. Anyone who’s ever learned how an XSS attack works has probably come across the img onerror method. This method involves using an XSS attack to create an image tag that has an invalid image URL, which causes an onerror event to trigger, running arbitrary javascript. By setting the name of a computer you create using the API, you can also get a stored XSS that runs every time the stalker opens the PCTT dashboard.
Conclusion
While this software has more holes than a block of swiss cheese, using the fact that Member IDs and Device IDs are sequential, I estimate there are only roughly ~62 thousand devices that have been affected by this spyware, over it’s lifetime, and there have been ~160 thousand total accounts ever created on this service. This is a relatively small number of impacted people but still, software like this is in a grey area, and it’s use is usually illegal, no matter what they say to try and convince you otherwise. By using this software as a stalker, or a victim, you are putting your privacy and security at stake.