Cyber Insurance Clarified: Essential Information You Should Have
In today's digital landscape, as data breaches and cyber attacks are becoming more and more common, businesses are recognizing the pressing need for protection against these threats. Cyber insurance has become as a crucial resource for companies looking to safeguard their assets and preserve their operational integrity. As the risks associated with cyber incidents change, understanding the nuances of cyber insurance coverage is crucial for every business owner.
Cyber insurance is not a universal solution, and its various components can be overwhelming. From data breach insurance to varied aspects of liability coverage, such as first-party and third-party cyber liability, it is important to understand the protections these policies provide. In addition, coverage for business interruption due to cyber incidents and the significance of cybersecurity risk management plays pivotal roles in ensuring that companies are equipped to navigate the 'challenges' of today's digital threats. Investigating these topics will offer valuable insights into how organizations can successfully mitigate their risks while ensuring their future.
Types of Cybersecurity Coverage
Cyber insurance comes in different forms to address the different risks linked to online operations. One of the main types of coverage is data compromise coverage, which shields organizations from the financial impact resulting from breaches to sensitive information. This type of coverage usually includes costs concerning legal fees, notification expenses, credit monitoring services for affected individuals, and public relations efforts to handle reputation damage following a breach.
Another significant category is first-party cyber liability, which focuses on safeguarding the insured organization from first-party losses incurred due to cyber incidents. This can include expenses related to data recovery, business interruption due to a cyberattack, and any necessary system repairs. Additionally, first-party coverage often includes provisions for lost income during the downtime caused by cyber events, making it essential for companies that depend on technology for their operations.
Lastly, third-party cyber liability coverage is designed to shield businesses from claims made by third parties affected by the organization’s cyber incidents. databreachservices.quora.com of insurance covers legal liabilities arising from data breaches or cyberattacks that compromise client or partner data. By offering protection against lawsuits and associated legal fees, third-party cyber liability plays a key role in an organization’s overall cybersecurity risk management strategy.
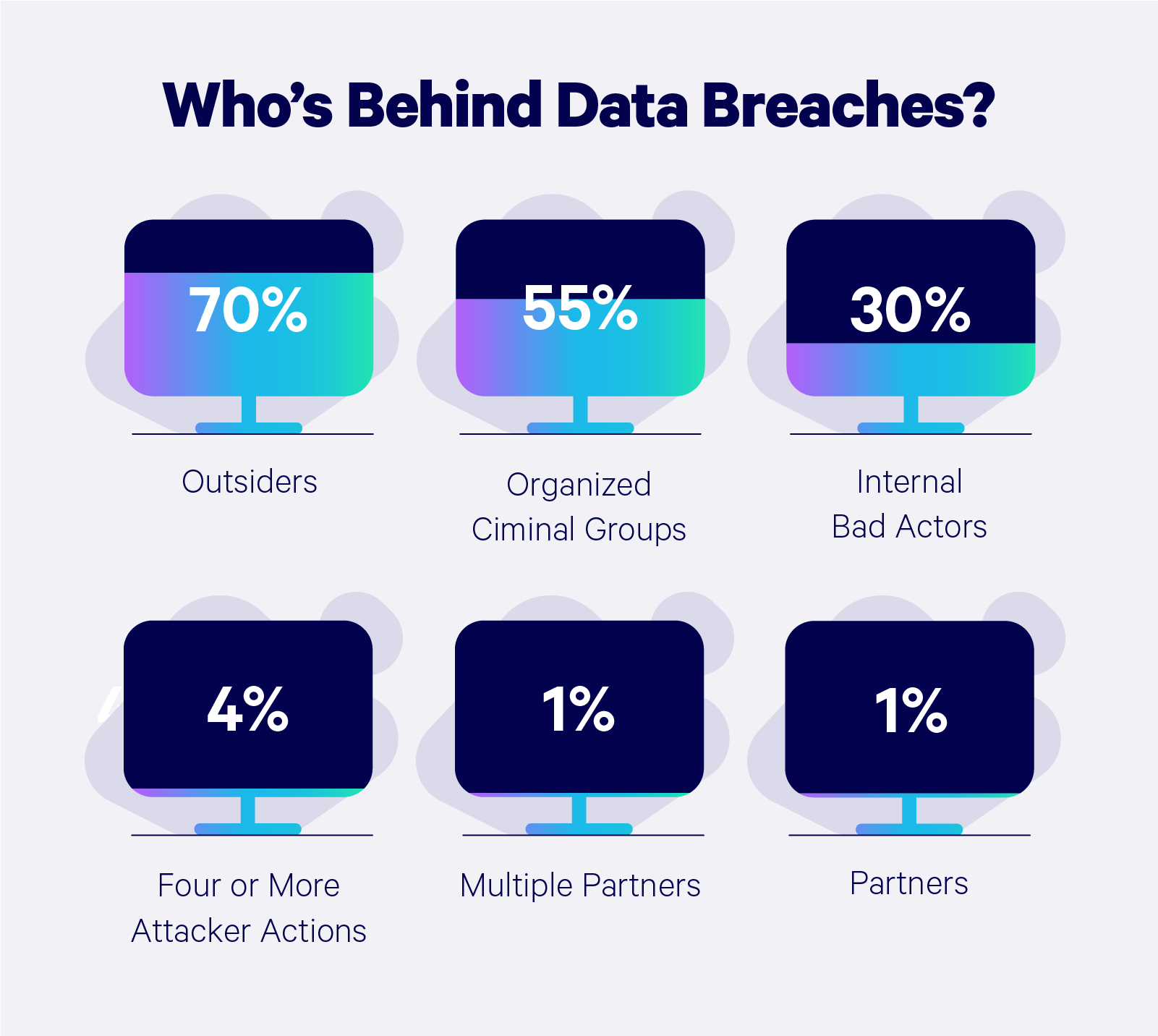
Understanding Cyber Risk
Cyber risk refers to the monetary dangers connected to the use of tech and the internet in corporate activities. As companies increasingly rely on online platforms to manage their functions, they expose themselves to multiple threats, such as data breaches and online assaults. This insurance is designed to mitigate these threats by providing protection for various elements of a cyber incident. Businesses need to understand these liabilities to protect themselves effectively from potential financial losses and legal liabilities.
One of the crucial aspects of this insurance is first-party cyber liability coverage. This form of coverage protects the business from damages that could directly affect its own operations. For example, if a data breach occurs, the expenses associated with notifying affected individuals, investigating the breach, and restoring systems could be included. This coverage ensures that businesses can bounce back from the immediate monetary effect of an incident without significant disruption to their processes.
In furthermore to primary insurance, organizations should also evaluate third-party cyber liability. This aspect of coverage protects against claims made by external entities, such as customers or associates, who may suffer losses due to a company’s data breach. This could include attorney costs, settlements, and other expenses related to lawsuits or damages claims. Comprehending both first-party and external risks is crucial for businesses to create a holistic cybersecurity risk management strategy that includes sufficient insurance coverage..
Information Security Threat Management Strategies
Establishing robust information security hazard governance approaches is essential for protecting private data and minimizing the potential consequences of online hazards. Firms should start by conducting a detailed threat analysis to pinpoint vulnerabilities in their systems and processes. This evaluation should consist of assessing existing security protocols, grasping likely risks, and evaluating the importance of the data at stake. By possessing a definitive understanding of wherein vulnerabilities lie, businesses can focus on their cybersecurity initiatives to combat the most critical risks.
In addition to threat analysis, continuous workforce development is a vital component of a holistic cybersecurity approach. Team members often function as the primary line of security against digital attacks, and arming them with understanding about information security standards can considerably reduce the risk of mistakes that contribute to data compromises. Regular training on identifying social engineering threats, creating robust authentication methods, and realizing the significance of information privacy can help foster a cybersecurity-conscious atmosphere within the company.
In conclusion, investment in advanced information security technologies is vital for ongoing protection. Companies should evaluate tools such as intrusion detection systems, security barriers, and encryption solutions to strengthen their defenses. Moreover, frequently updating software and systems can close security gaps that attackers take advantage of. By combining advanced tools with a solid threat management strategy, organizations can boost their resilience against cyber incidents, guaranteeing that they are better prepared for potential breaches while also satisfying their cyber insurance coverage.