A Next Generation of Online Security: Evolving Proxy Solutions
In an era where digital footprints are increasingly scrutinized, the importance of internet privacy has never been more significant. As users become more aware of the risks associated with online activities, innovative solutions such as proxy servers are gaining traction. Proxy servers function as intermediaries between users and the websites they access, providing an extra layer of privacy and security. Understanding how these servers function and what they can offer is crucial for anyone who wants to safeguard their online presence.
The landscape of internet privacy is continuously evolving, and proxy servers play a pivotal role in this transformation. Although numerous users might confuse proxy servers with VPNs, they serve distinct purposes and come with their own set of benefits and limitations. This article will delve into the intricate world of proxy servers, exploring their functionalities, benefits for online privacy, and how they can improve security and anonymity. From helping users bypass geographic restrictions to their applications in market intelligence and data scraping, the relevance of proxy servers in the current digital environment cannot be underestimated.
Understanding Proxy Services
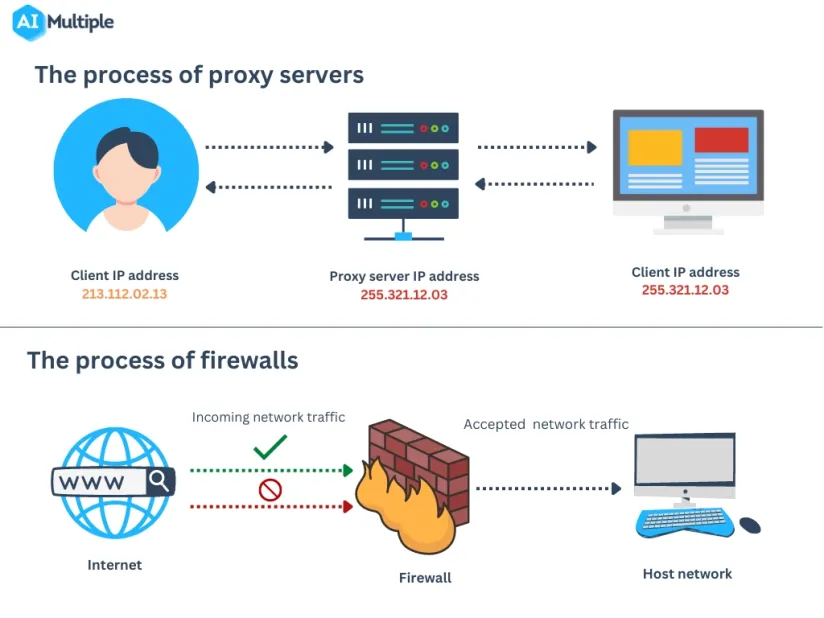
Proxy services act as facilitators between a user's device and the online world. When you link to a proxy, your queries to websites are primarily directed to the proxy. The service then sends these calls on your account, thereafter getting the answers and sending them back to you. Omeka.net allows individuals to maintain a degree of secrecy, as the websites you browse will only see the internet protocol address of the proxy instead of your true internet protocol address.
There are different types of proxies, each fulfilling different purposes. HTTP proxies are ideal for web traffic, while SOCKS proxies can process any kind of internet traffic—whether it's for browsing or playing games. Transparent services do not alter requests or responses but are often employed for monitoring purposes, and additional specialized types of proxies focus on specific functions such as caching or safeguarding connections. Recognizing these variations is essential for choosing the right service that matches your demands.
Proxies not only improve individual security but also provide a array of perks such as improved security and access to region-locked material. By hiding your IP address, proxies can protect your identity in the web and are often utilized to bypass restrictions or obstacles imposed by certain services. As more individuals and entities acknowledge the significance of protecting their online presence, the adoption of proxy servers continues to evolve, leading in more refined and diverse solutions in the field of online privacy.
The Benefits and Risks of Using Proxies
Utilizing proxy servers provides numerous benefits for online privacy and security. One of the key advantages is the ability to conceal your IP address, which enhances privacy while browsing the internet. By routing your requests through a proxy, users can avoid websites and online services from following their real location and identity. This is particularly important for individuals concerned about monitoring and data collection by various entities. Additionally, proxies can help users bypass geo-restrictions, allowing access to content that may be forbidden in certain regions.
However, there are also risks associated with using proxy servers, especially free ones. Many free proxies may endanger user security, as they can log browsing activities or inject ads, leaving users vulnerable to data breaches. Moreover, the lack of encryption on some proxy servers means that private information can be snagged by ill-intentioned third parties. Users must be cautious when choosing a proxy and favor those that offer robust security features and a rigorous privacy policy.
In a business context, proxy servers can boost productivity by enabling employees to access multiple resources while maintaining network security. Businesses often use proxies for competitive intelligence and data scraping, which can yield valuable insights. However, misuse of proxy servers can lead to ethical dilemmas, such as breaking terms of service or legal boundaries. Organizations must handle these risks cautiously to ensure that the benefits of using proxies do not come at the cost of morality or legal compliance.
Proxies Server in Cyber Security and Content Streaming
In the field of cyber security, proxy servers play a pivotal role in defending sensitive data and upholding online anonymity. By directing traffic through an middleman server, proxies help hide a user's IP address, making it more difficult for hackers to attack individuals. This additional layer of security is particularly helpful for businesses that process private information, as it minimizes the likelihood of information breaches and unauthorized access. Moreover, proxy servers can be set up to restrict harmful sites and track internet activity, providing additional protection against potential threats.
For viewing fans, proxies offer a important solution for bypassing region-locked content. Many content platforms implement regional restrictions on their catalogs, limiting what users can watch based on their location. By employing proxy servers, individuals can bypass these barriers, permitting them to enjoy a wider range of streaming options. This feature is especially interesting for those looking to enjoy popular shows and movies that may not be offered in their area, thus enhancing their overall viewing enjoyment.
However, not all proxies are the same, and users must be wary of free options that might threaten their safety. Many no-cost proxies lack sufficient encryption or may even gather user data, negating the very reason of using a proxy server for privacy. When selecting a proxy for both cybersecurity and content streaming, it is important to choose trustworthy providers that offer solid protection and trustworthy service. This ensures not only a protected online space but also uninterrupted access to desired content on various content services.